Security and Permissions
make87 provides robust security measures to protect your distributed AI applications, coupled with granular permissions management for collaborative environments.
Network Security
make87 implements strong security protocols for network communication:
- Encrypted Overlay Network: Utilizes Noise protocol framework (Curve25519, ChaCha20-Poly1305).
- Automatic Key Rotation: Regularly updated encryption keys for enhanced security.
- Secure Node Authentication: Nodes authenticate securely with the make87 control plane.
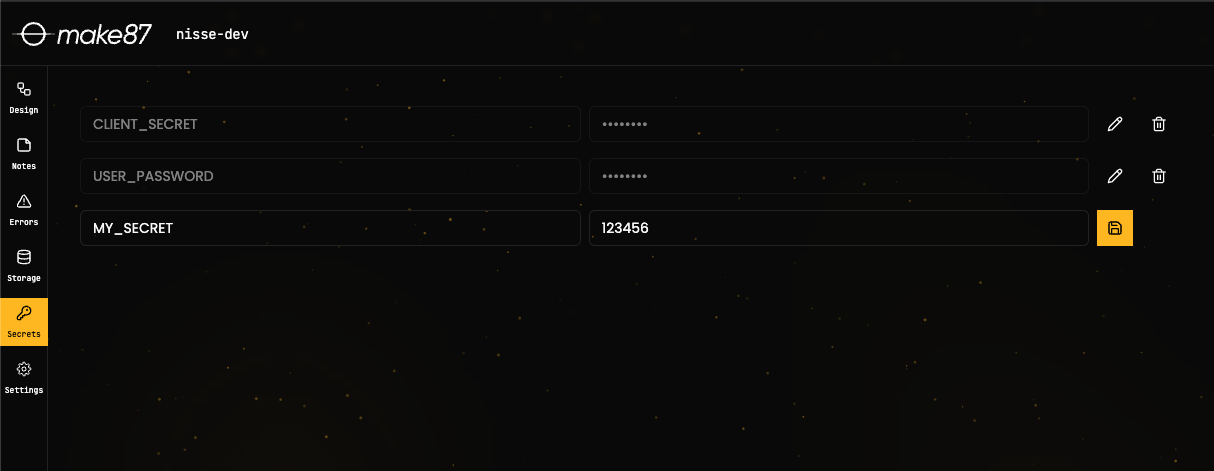
Secrets Management
make87 manages sensitive configurations and credentials securely:
- Encrypted secrets vault integrated directly into the platform.
- Secrets are mounted securely within containers as read-only files at
/run/secrets/{SECRET_NAME}.secretif they are used in an application. - Secrets are configured on a per-system basis, allowing different secrets for different systems or applications.
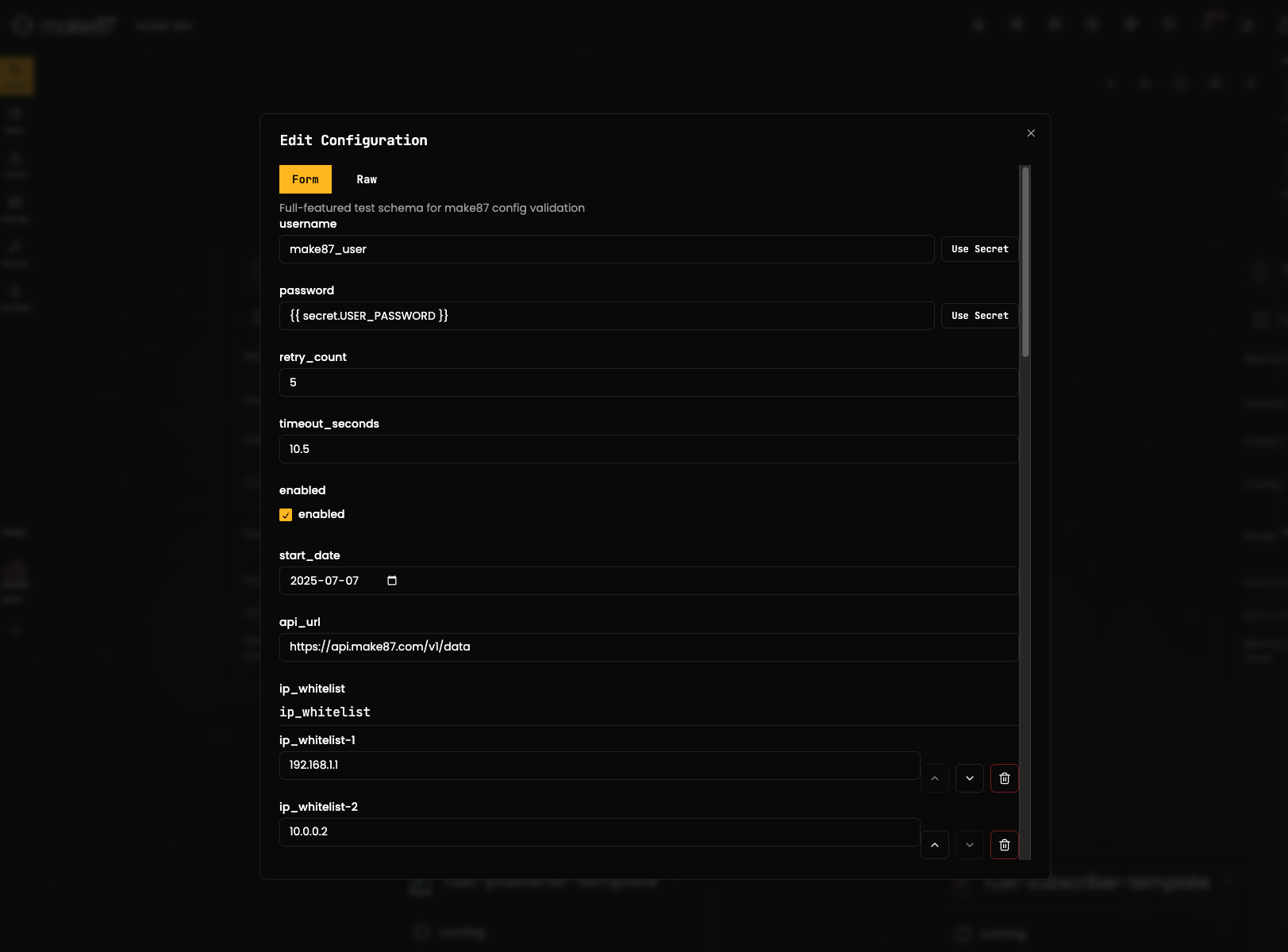
Using Secrets in Applications
Secrets can be referenced in your application configuration using the {{ secret.SECRET_NAME }} syntax.
With Official SDKs (Recommended)
When using make87's official SDKs (Python, Rust, etc.), secrets are automatically resolved when loading configuration. The SDK handles secret file reading transparently:
from make87.config import load_config_from_env, get_config_value
# Load configuration - secrets are automatically resolved
config = load_config_from_env()
# Access the resolved secret value directly
db_password = get_config_value(config, "DATABASE_PASSWORD")
Manual Secret Access
If you need to work with environment variables directly or aren't using an official SDK, you can access the mounted secret files manually:
# Secrets are mounted at /run/secrets/{SECRET_NAME}.secret
with open('/run/secrets/DATABASE_PASSWORD.secret', 'r') as file:
db_password = file.read().strip()
Access Control and Permissions
make87 allows detailed permission management:
Resource Ownership
| Scope | Simple Access Rules | Advanced Access Rules |
|---|---|---|
| Owner | Single user or organization that creates the resource | - |
| Resources (Applications, Nodes, Systems) | User or Org-level read, write, delete; public read-only | Rule-based selectors for granular permissions (specific users or orgs) |
Organizational Spaces
- Every user has a personal workspace.
- Team and Enterprise licenses include organizational spaces.
- Resources within an organization inherit permissions defined by the organizational policies.
Best Practices for Security
- Regularly rotate keys and secrets.
- Minimize resource permissions (principle of least privilege).
- Regularly review audit logs for unusual activity.